Are you a Telegram user? Would you like to install the Desktop version of the app?
Then be aware, because a malicious installer of the instant-messaging platform has been reported by cybersecurity experts, despites its capacities to evade several antivirus engines.
We’re talking about the Purple Fox rootkit, distributed through email or phishing sites.
Purple Fox Rootkit Inside Telegram Desktop Installer
It was Minerva Labs who announced the attack this Monday.
How did they detect the Purple Fox Rootkit inside this Telegram Desktop Installer, despite hiding from detection software like Avira, McAfee, Panda, and many more?
The attack goes under the radar by dividing its files into several small ones, with very low detection rates. This way, the malicious parts are camouflaged with the resting legitimate software, leading to the Purple Fox rootkit infection at the final stage.
As mentioned in the introduction, the attack’s script named “Telegram Desktop.exe” includes the actual Telegram Installer and a malicious downloader carrying the Purple Fox malware.
In plain sight, the file with the Telegram icon goes even more unnoticed by bearing the original white paper plane.
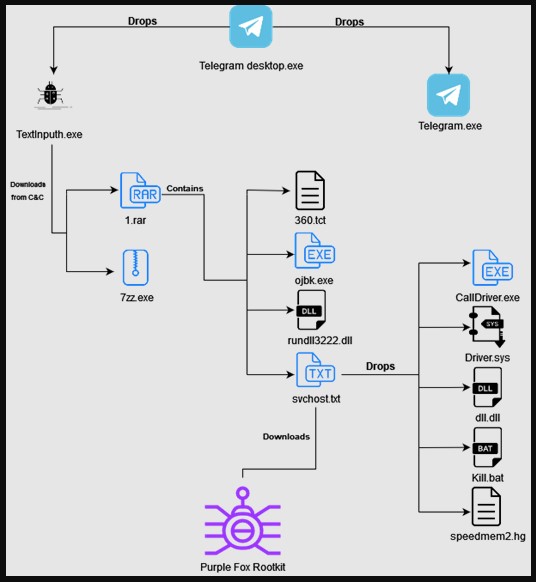
What the installer does, is to create a new folder named “TextInputh” under C:\Users\Username\AppData\Local\Temp\ and drop both the malicious TextInputh.exe downloader and the non-executable Telegram installer. The first is the one to execute.
Then, this TextInputh.exe downloader creates a new folder named “1640618495” under the C:\Users\Public\Videos\ directory and proceeds to execute the C2 (command-and-control) server which downloads a RAR (containing the payload and configuration files) and legitimate 7z archive, which unpacks everything onto the ProgramData folder.
Once the machine is compromised, TextInputh.exe performs the following actions:
- Copies 360.tct with “360.dll” name, rundll3222.exe, and svchost.txt to ProgramData folder,
- Executes ojbk.exe with “ojbk.exe -a” command line,
- Deletes 1.rar and 7zz.ex then exits the process.
Next, the rundll3222.dll disables UAC, scvhost.txt is executed, and five other files are dropped in the system: Calldriver.exe, Driver.sys, dll.dll, kill.bat, speedmem2.hg.
They collectively block the initiation of 360 AV processes and also prevent the detection of Purple Fox malware on the compromised machine, so it can gather basic system information, check if security tools are running, and finally send trash to a C2 address.
If the reconnaissance process is completed, then Purple Fox downloads from the C2 as a .msi file containing encrypted shellcode for both 32 and 64-bit systems. The infected machine restarts automatically for the new registry settings to take effect and disable User Account Control (UAC), giving administrator privileges to the malicious program.
That’s why it’s always recommended to keep UAC active on your OS at all times.
Now, it’s still unknown how this malware, in particular, got distributed, but similar ones have always been distributed via shady forums, software sites, and YouTube videos.
What is the Purple Fox Rootkit?
The Purple Fox malware can be planted beyond the reach of detection/security tools. It was first discovered in 2018 and mentioned back in March 2021 inside a Guardicore report that mentions the details of its work-like propagation and backdoor ability.
A few months later (in October 2021), Trend Micro researchers uncovered a .NET implant dubbed FoxSocket delivered along Purple Fox to make use of WebSockets. After that, the same company sed light on a new Purple Fox infection chain that targets SQL databases to insert malicious common language runtime to stealthily run illicit cryptocurrency mining.
Now, can this threat affect you?
It definitely can. If you found this article is more or less because you got affected or fear of doing so. We can solve whatever is your case (and we can do it now).